Summary
The following updates have been made within the Data Exchange functionality:
- Support for token-based authentication for gateway integration endpoints and the REST Direct outbound integration endpoint delivery plugin
- mTLS support for outbound HTTP traffic
- REST Direct property removed
- Excel 2003 has been removed as an export option
- New proxy support for HTTP-based endpoint plugins
- Kafka connector SASL authentication added
Details
Support for token-based authentication for gateway integration endpoints and the REST Direct Outbound Integration Endpoint delivery plugin
Now, gateway integration endpoints and the REST Direct outbound integration endpoint delivery plugin support token-based authentication. Most REST services do not support basic authentication, instead requiring some form of token-based authentication where a token is obtained via one endpoint and passed via request headers with each request to the service (typically the Authorization header). Some services make use of standards like OAuth 2.0 for this purpose, while others are non-standardized.
To support both standardized and non-standardized ways of obtaining and passing tokens, new functionality has been added for gateway integration endpoints and the REST Direct outbound integration endpoint delivery plugin that delegates the responsibility of building the required headers to a highly flexible business function. The framework will for both call the business function when a new token is required.
For more information on the OIEP authentication options available, refer to the REST Direct Delivery Method topic in the OIEP section of the Data Exchange documentation here. For more information about the Gateway Integration Endpoint authentication options, refer to the Configuring a Gateway Integration Endpoint - REST topic in the Gateway Integration Endpoints section of the Data Exchange documentation here.
Additionally, a new ‘Secret’ bind option has been added for JavaScript business actions, conditions, and functions. This bind option allows script access to secrets like passwords and client credentials without compromising security. For more information on the 'Secret' bind, refer to the Other Binds topic in the JavaScript documentation here.
mTLS support for outbound HTTP traffic
STEP now supports Transport Layer Security (TLS) with mutual authentication (mTLS) for outbound HTTP traffic. mTLS is more secure than TLS, as it requires both the server and client to verify each other before data is transferred.
This functionality is controlled via a set of configuration properties for the key store and trust store to use across all features. These configurations must be set in sharedconfig.properties on the STEP application server.
SSL.Default.KeyStore.Location – Full path to the key store file in the file system. For clusters, the key store must be in a directory accessible from all application servers.
SSL.Default.KeyStore.Password – Password for the key store.
SSL.Default.KeyStore.Type – The type of key store. This defaults to 'JKS.'
SSL.Default.TrustStore.Location – Full path to the trust store file in the file system. For clusters, the trust store must be in a directory accessible from all application servers.
SSL.Default.TrustStore.Password – Password for the trust store.
SSL.Default.TrustStore.Type – The type of trust store. This defaults to 'JKS.'
This mTLS functionality has been tested with the gateway integration endpoint REST plugin, the REST and REST Direct outbound integration endpoint delivery plugins, and URLConnections directly from business rule JavaScript.
Note: mTLS will not work in combination with the REST gateway integration endpoint plugin 'SSL trust store location' and the existing REST Direct mTLS functionality configured via properties 'RESTDeliverySSLKeyStoreLocation,' 'RESTDeliverySSLKeyStorePassword,' and 'RESTDeliverySSLKeyStoreType.'
For more information on mTLS, refer to the Mutual Transport Layer Security topic in the Data Exchange documentation here.
REST Direct property removed
The 'RESTDirectAndDelivery.MaxConnectionsPerRoute' property has been removed from STEP 10.2, as it is no longer necessary. If this property is set, it will not be possible to start a 10.2 system until the configuration property has been removed.
Excel 2003 export / import formats removed
Excel Office 2003 was desupported with the 10.1 release, and with this release, the option to use desupported Excel versions for imports and exports has been removed from the Stibo Systems Enterprise Platform (STEP) interfaces.
Customers using unsupported Excel versions were advised in the 10.1 release notes to convert import and export files, older Smartsheet versions, translations, eCatalog files, etc., to a supported version and resave prior to upgrading to 10.2 (i.e., open XLS files and resave as XLSX files). With the 10.2 development, saved configurations that have not already been converted will work but export as Excel 2007+.
Proxy support for HTTP-based endpoint plugins
For HTTP-based outbound delivery methods for outbound integration endpoints (OIEPs), receiver methods for inbound integration endpoints (IIEPs), and gateway integration endpoints (GIEPs), a new Proxy Config parameter is available for customers that need the extra security and privacy of passing through a proxy server with its own login requirement.
HTTP proxy configurations are defined via properties saved in the sharedconfig.properties file. Multiple proxy configurations can be made by giving them different names. Also, each proxy configuration has its own property for Host, Port, User, and Password.
For example: A proxy configuration named Sample1 can be defined as follows:
Http.ProxyConfiguration.Sample1.Host=localhost Http.ProxyConfiguration.Sample1.Port=8080 Http.ProxyConfiguration.Sample1.User=user Http.ProxyConfiguration.Sample1.Password=password
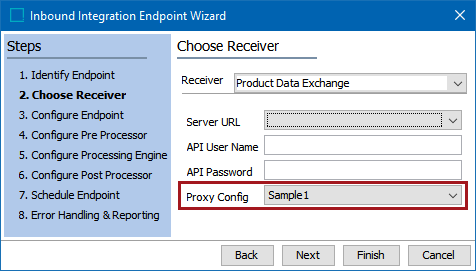
Endpoint plugins that utilize the properties outlined above and the Proxy Config are:
- Microsoft Azure Blob Storage (GIEP)
- Product Data Exchange (IIEP & OIEP)
- REST (OIEP)
- REST Direct (OIEP)
- SalesforceREST (GIEP)
- Salesforce Merge Delivery (OIEP)
- Salesforce Receiver (IIEP)
- Salesforce Update Delivery (OIEP)
For more information regarding HTTP proxy configurations, refer to the HTTP Proxy Configurations topic in the Data Exchange documentation here.
SASL authentication now supported by Kafka Connector
Support for Simple Authentication and Security Layer (SASL) authentication has been added for the Kafka receiver and delivery plugins that were introduced with STEP 10.1. Both PLAIN and SCRAM are supported. This enhancement increases data security options while expanding the current Kafka connector authentication functionality support, which includes support for AWS MSK, Heroku, and Aiven (with TLS client certificate authentication).
After installing STEP 10.2, properties need to be added to the sharedconfig.properties file to configure the PLAIN and SCRAM authentications. Refer to the Considerations for Setting up Kafka Receiver or Delivery topic in the Data Exchange documentation (here)