When creating attribute groups to be used with Action Sets, it is important to create the attribute group with a role and general function in mind. Whether this is for a user to enrich items, for a supplier to review items, etc., having an attribute group created specifically for a particular User Action group, creating a one-to-one correspondence, makes maintenance of the group easier.
Note: The exception is if the same role should have the same privileges for different nodes.
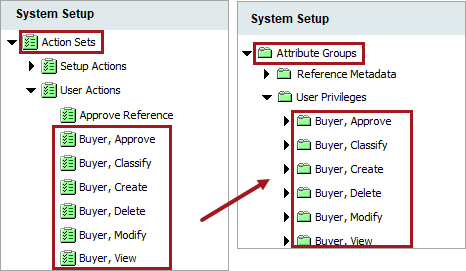
It is recommended practice to create only the attribute groups intended for user privilege application and action sets that are valid for the role.
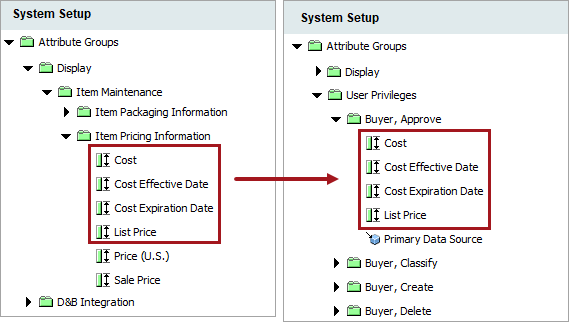
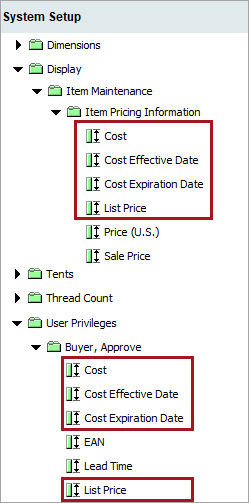
For example, an administrator wants a user to update the 'Cost,' 'Cost Effective Date,' 'Cost Expiration Date,' and 'List Price' for products in the system. They do not want them to touch the 'Price (U.S.),' or the 'Sale Price' attribute for products in the system. The administrator creates the 'Buyer, Approve' attribute group created for user privilege application, links the needed attributes to this group, and applies the necessary user privileges to this group. Now the user is able to access only the necessary attributes to fulfill their role's requirements.
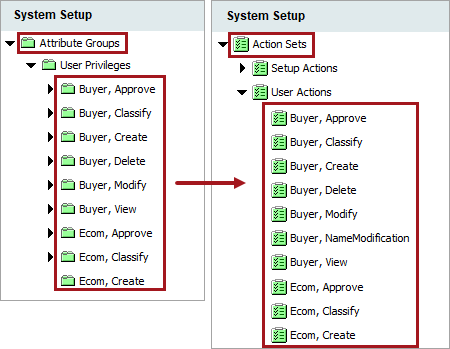
Note: Action sets align almost one-for-one with the attribute groups used for user privileges. The exception is in the case of the Images and Documents groups. For these, there are Action Sets for 'Classify' but no attribute groups for 'Classify.' This is because only attributes and reference types get linked into the attribute groups. With digital assets, there is not a reference type for the asset to classification link. In cases where there are classification reference types or product to classification Link types, create an attribute group for those reference types and link them in.
Setting up attribute groups this way aids in long term maintenance. If a certain role needs to start or stop doing an action, either:
-
Add or remove the action(s) from the action set
-
Add or remove an attribute or reference type from a group
-
Add or remove a privilege rule completely
For more information on how to perform these tasks, refer to the Maintaining Action Sets topic.
Considerations for Supplier Privilege Configuration
-
If a supplier user is linked into multiple supplier groups, the supplier can review all of the supplier hierarchies that they are a member of.
-
If products or assets are linked into a multiple supplier’s hierarchies, the supplier will not be able to review them.
Users and Dimension(s)
If User Actions are restricted to a dimension, keep the following in mind:
-
Users are only able to modify the dimension‑dependent attribute values.
-
Users are not able to modify values that have no dimension dependency.
For more information on restricting actions using dimension points, refer to the Privilege Rules topic.
Creating Attributes Groups Specifically For Use with User Privileges
To create attributes groups specifically for use with user privileges, follow the example below.
In this example, the attribute groups and user privileges are being applied to products, but the same concept can be applied for suppliers.
-
Create attribute groups that will be used only for privileges.
-
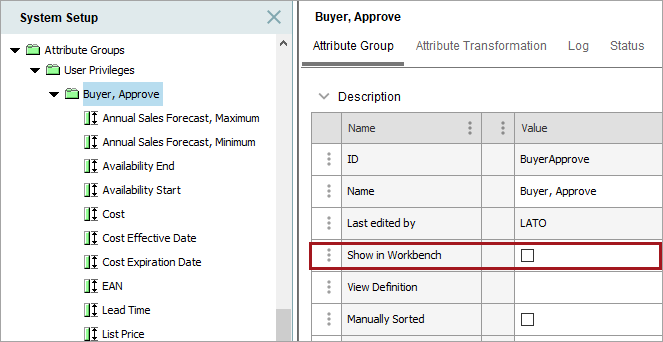
Deselect the 'Show in workbench' field on the attribute group being created.
-
Create attribute groups that mirror the Action Sets for each role. Doing this eliminates the problem of trying to make attribute groups intended for display to align with privileges. Attribute groups planned for display were not intended for this use case.
-
Link allowable attributes from their main groupings to the user privilege groupings. To do so, go to System Setup and either:
-
Click on the desired attribute and drag it to the new attribute group that it should be a part of.
-
Click on the desired attribute, go to the References tab, and under the 'In Attribute Group' flipper, click Add Attribute Group. Select the desired attribute group to add.
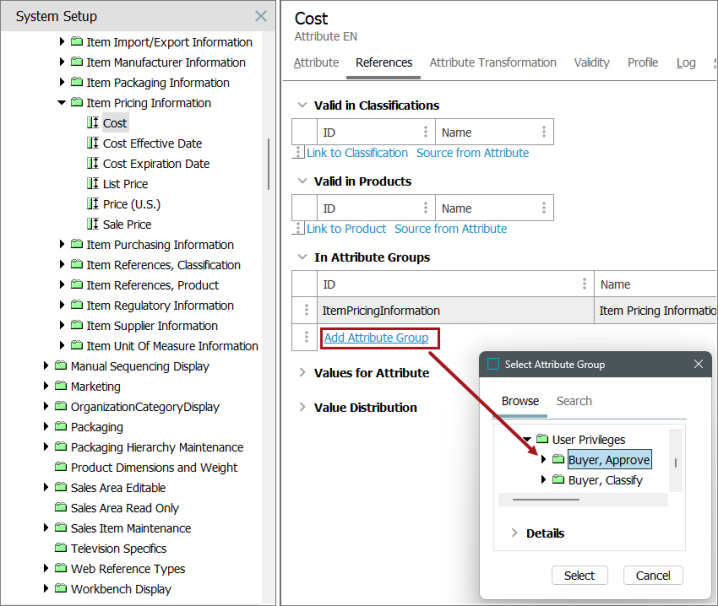
Note: Do not link the Category Specific attributes unless there really are restrictions within this group, since there are a great number of Category Specific attributes. Use separate privilege rule(s) to better handle Category Specific attributes and any sub‑groups.
Important: In case of numerous attributes (e.g., if you use standards like ETIM and eCl@ss without merging attributes), be aware that working with groups with more than 10,000 attributes may cause performance issues when updating attribute links to groups. Also note that sub-groups can be defined for each user privilege group. Rules will apply to all attributes linked to sub-groups.
-
-
Link all allowable reference types to the user privilege attribute groups. For more information on how to link references to attribute groups, refer to the Maintaining a Reference Type topic.
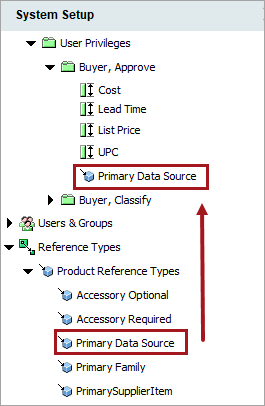
Note: Linking reference types to attribute groups using STEPXML as a template can save time. For more information on STEPXML, refer to the STEPXML Format topic in the Data Exchange documentation.
-
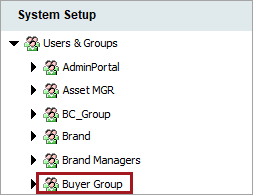
Go to the Users and Groups node, and click on the desired User Group. In this example, it is Buyer Group.
-
Add the necessary privilege rules on the Privilege Rules tab on the desired User Group. For more information on how to configure privilege rules, refer to the Privilege Rules topic.
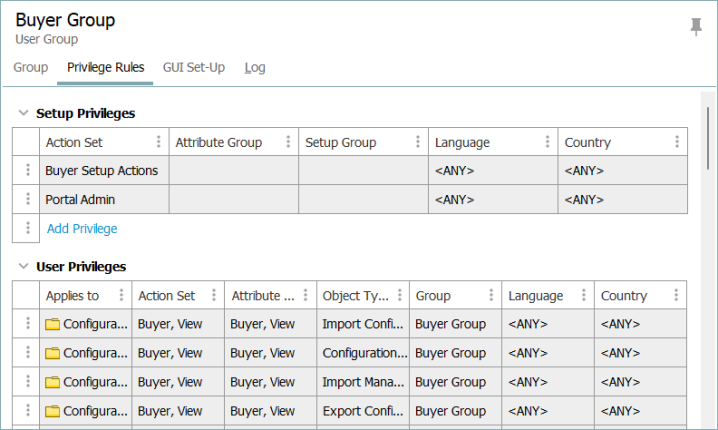
When creating privilege rules, match up User Action sets with the privilege attribute groups created in the previous steps. Do this for each applicable object type.
Often, privileges should not be valid for all object types, and the rule needs to be repeated for each allowed object type. If the role can perform a general function on all object types below the root, leave the Object Type field blank.
Important: For Suppliers, only apply privilege rules to the supplier root. Individual supplier’s privileges are limited to their own products, assets and batches. It is not necessary to apply privileges to each suppliers root.
Note: Privileges on product object types can be defined on classification nodes (for products classified below the given nodes).