When dealing with customer data, some of the data is sensitive and needs extra protection. Encrypting an attribute is a way of making its values inaccessible to STEP users who are not allowed to view the values as well as obscuring the data for enhanced security. An attribute should only be encrypted when necessary since it prevents useful functionality such as searching, data profiling, exporting, and more.
Encrypted attributes require a password to view or edit the values of the attribute. Before creating an encrypted attribute, create a cryptographic key.
Cryptographic Key
To create a cryptographic key, go to System Setup > Users and Groups > Cryptographic Keys flipper > click Create Cryptographic Key.
The attribute encryption system implemented in STEP is based on AES 256 bit encryption. It is a symmetric key algorithm which means that the same key is used for encryption and decryption. The system can hold multiple keys, and each key can have one unique password. This password then will be shared between users. For instance, the members of a specific group could be the only ones that should have access to the values of attributes Attr_A and Attr_B. In that case, only one key would be used for encryption of the values of Attr_A and Attr_B, and the password of the key would be shared among the users of the group.
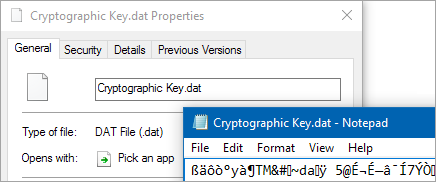
When creating a new cryptographic key in STEP, a 32 byte file with the actual key is required. Keep this key file in a safe place, possibly encrypted as well, where it will remain secure. In addition to the key file, an ID and a password must be supplied.
Note: Cryptographic keys are stored in STEP protected by a password that is neither the original key, nor the original password.
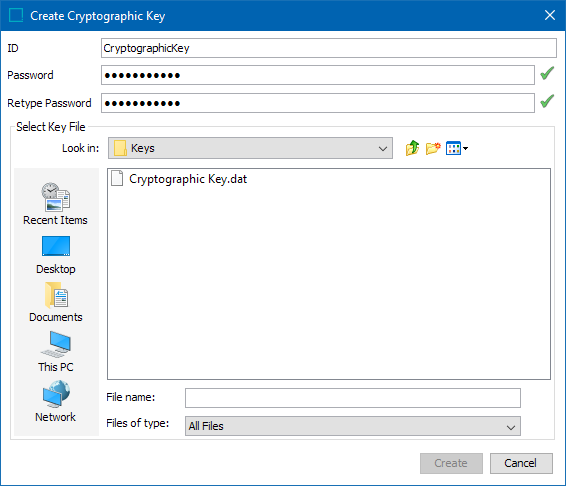
The ID is shown to users when prompting for the password. Therefore, the ID should be human-readable. The password is required each time attributes using this key are encrypted or decrypted.
The password can be changed when a cryptographic key has been created. After changing the password, all attributes using the cryptographic key use the new password, but the data values are not modified.
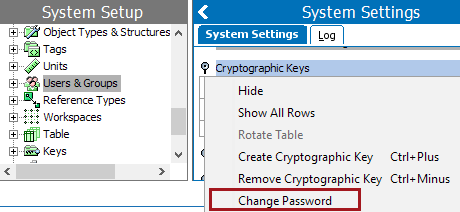
Password requirements
The minimum requirements for passwords are 8 characters containing at least three of these four groups:
- Lower case characters a-z
- Upper case characters A-Z
- Digits 0-9
- Symbols
The setup action 'Maintain cryptographic keys' is required to create or delete cryptographic keys, and to change their passwords.
Creating Encrypted Attributes
When creating a new attribute, it is possible to select an encryption key. To do so, follow the steps below:
- Go to System Setup ad expand the attribute groups node.
- Select and right-click on the desired attribute group under which the new attribute is to be created, and click on ' New Attribute'.
- On step 2, Enter ID and Name, there is an option called 'Cryptographic Key' with a dropdown list. Select the appropriate Cryptographic Key and proceed.
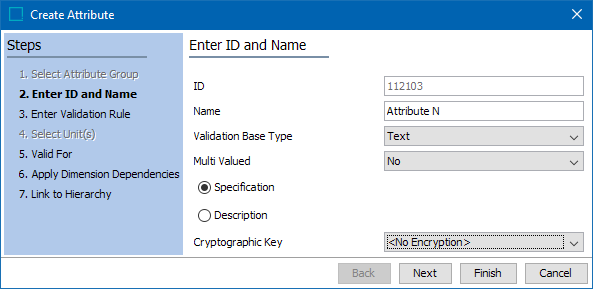
Note: The cryptographic key cannot be changed or set after creation.
Properties of attributes that cannot be used with encryption
- LOV validation - since an LOV can be shared between multiple attributes, it cannot be encrypted.
- Full Text Indexable - because the value is stored encrypted, this would represent a security risk.
- Calculated - a calculated value is usually not stored as a value, but derived from other data.
- The validation rules cannot be changed after creation, except multi-valued if the data allows it.
Accessing encrypted data
An encrypted attribute will not initially show any value in STEP Workbench or Web UI. Instead, a Decrypt button displays in its place. Clicking this button prompts the user for the cryptographic key file password for the key file used on the attribute.
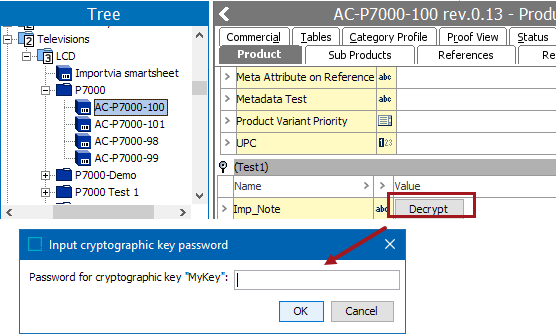
When the correct password is entered, the attribute looks like any other attribute, showing its value. In this state, it is also possible to edit the value. The client remembers the password for the key file for a limited time, which allows editing multiple attributes without having to re-enter the password.
Each time a user decrypts an encrypted attribute, it is logged in the System Setup Log (available via workbench).
Restrictions of Encrypted Data
- Encrypted data cannot be recovered if the key or password is lost. Keep a backup of the original key file used when creating the key in STEP.
- Keys cannot be exported from or imported into STEP.
- Encrypted attributes cannot be exported.
- Encrypted attributes cannot be profiled in data quality.
- It is not possible to search for values of encrypted attributes.
- It is not possible to add / remove encryption to an attribute after it has been created.
- Background processes cannot access encrypted values.
Important: When using encryption in STEP, it is very important that the system is set up to use https, otherwise passwords, values to be encrypted, and decrypted values are transferred in clear text and security is compromised.