Admin users can configure security settings related to passwords to ensure that STEP users adhere to the required password security level.
Important: Passwords for the 'stepsys' and 'DBA' user accounts on production and preproduction environments are required to use a specific, fixed, strict password policy independent from the Security Policy. The password for these two accounts:
-
must be at least 16 characters and meet three (3) of the following four (4) criteria: must contain a minimum of one lowercase character, must contain a minimum of one uppercase character, must contain a minimum of one digit, must contain a minimum of one special character.
-
does not expire.
-
is reusable after 24 hours.
The two accounts are locked out for 15 minutes after three (3) failed log in attempts.
This applies only to users authenticated by STEP. It does not apply to externally maintained users who are authenticated through an external authentication system, such as Azure AD.
To access the password settings, on the System Setup tab, select the Users & Groups node. Scroll down to find the Security Policy flipper, which includes the following settings, shown below:
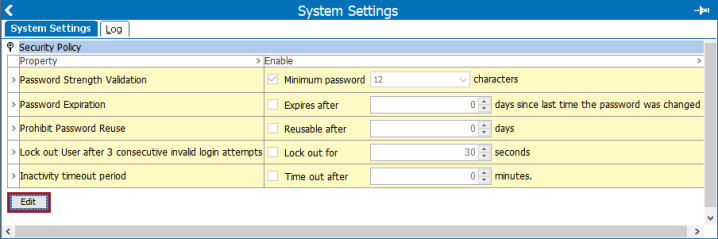
Important: Changes made to these parameters will be applied to all user groups located under the Users & Groups node. These settings cannot be customized for single users or user groups.
To change the Security Policy parameters, click the Edit button below the parameters to display the Security Policy edit dialog.
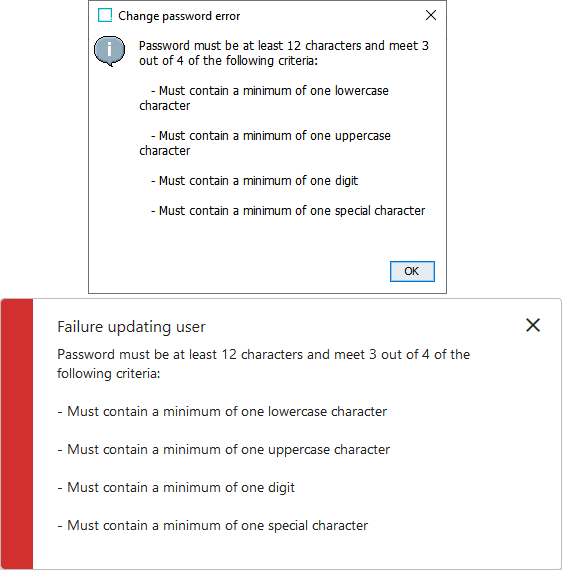
- Password Strength Validation – When checked, new passwords must conform to at least three of the four requirements intended to ensure a strong password.

-
Must contain a minimum of one lower case character
-
Must contain a minimum of one upper case character
-
Must contain a minimum of one digit
-
Must contain a minimum of one special character
Additionally, the password must meet the minimum password character requirement, which ranges from the default of eight (8) characters to the maximum of 20.
If not all password requirements are met, the following error displays in the workbench and in Web UI.
- Password Expiration – When checked, all new passwords will expire after the set number of days have passed. Once a password has expired, upon the next log in attempt, login will fail, and an 'Invalid username or password' message will display. Verify that you have entered the correct username and password for authentication. If you have, then the message likely indicates that your password has expired and needs reset. If you continue to have issues, contact your system administrator.

Note: Passwords can be set to not expire for a user group via the Group tab for a specific user group. Refer to the Working with User Groups topic for more information.
- Prohibit Password Reuse – When box checked, the system prohibits a user from reusing old passwords. Old passwords are unavailable for reuse based on the set number of days.
- Lock out User after 3 consecutive invalid login attempts – When checked, three (3) failed attempts to log in by entering a wrong or mistyped password will prohibit any new log in attempts for the set number of seconds.
Note: Administrators who reset passwords for users locked out of the system also reset the time-out period for those users.
- Inactivity timeout period – When checked, the system can be configured to automatically sign out any logged-in user from the workbench and Web UI once the set number of inactive minutes is reached. This setting is most appropriate for STEP systems with a large number of active users.
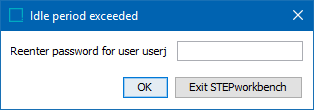
Once the inactivity timeout period is reached, the following dialog is displayed for the logged out user, and the password must be entered to resume work in the workbench.
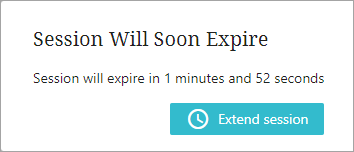
Web UI users will get a popup dialog when there are two (2) minutes left before the inactivity timeout period is reached. You can choose to extend your session to avoid automatic logout.
As an additional, but unrelated security measure, the workbench token renewal time is required every four hours by default. While increasing that time also increases token-related security risks proportionally, modifications can be made via the sharedconfig.properties file. Include the case-sensitive property text 'Step.Token.ExpiryTimeInHours=[hours]' to set a time between five and 72 hours. For example, Step.Token.ExpiryTimeInHours=5.
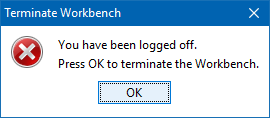
When the expiry time is reached for the workbench users, the Terminate Workbench dialog shown below is displayed and the user is logged out.
When the expiry time is reached for Web UI users, they are logged out and returned to the Web UI login screen.